NamPoHyu encrypter provides remote encryption of Samba servers
- Roman Sologub
- Sep 10, 2020
- 1 min read
The new encrypter family called NamPoHyu Virus or MegaLocker Virus attacks its victims slightly differently than other encrypters. Instead of launching the encrypter on the victim's computer, phishers launch it locally on their systems and allow it to encrypt remotely accessible Samba servers.
Usually, traditional encrypters are delivered to the victims’ computers via phishing emails, portable storage devices, etc. In the present case, the encrypter searches for accessible Samba servers, brute forces passwords and remotely encrypts their files.
Samba is an open-source implementation of the network protocol Server Message Block (SMB) used to provide services such as file and print sharing. It works in most systems with Unix or Unix similar operating systems and allows these systems to interact with clients on the Windows basis.
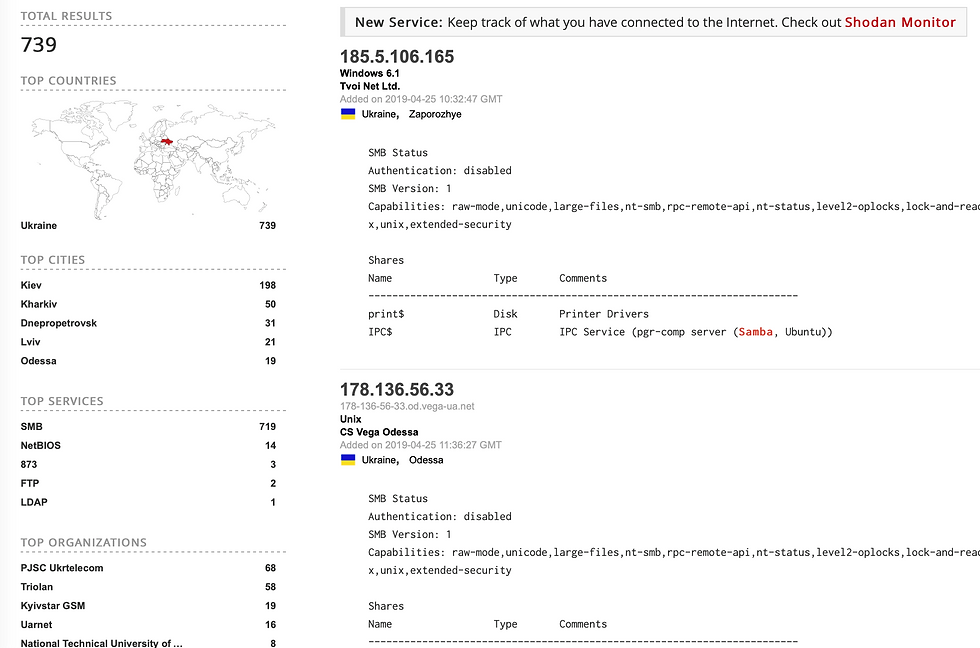
BleepingComputer researchers report that currently there are 500,000 unauthorized and publicly accessible Samba servers. They received this data via the Shodan service.

In Ukraine, ISSP researchers found 739 accessible Samba servers. Organizations which have the largest number of actuations include: Ukrtelecom, Triolan, Kyivstar, Uarnet and NTUU "KPI".
During the encryption, the .NamPoHyu extension is added to the extension of the encrypted files and a ransom demand file !DECRYPT_INSTRUCTION.TXT is created.


Recommendations
To guard against this type of encrypter, you need to comply with the following recommendations:
- make backup copies of the systems;
- close all the unused ports in the systems;
- do not connect services of remote desktops directly to the Internet. Instead, make sure that they can only be accessed via VPN:
- update all potentially vulnerable applications;
- carry out continuous monitoring of abnormal activity in your network;
- use special software for behavioral identification of threats and white list technologies.



Comments